In the previous article, IPv6 DDoS is now a threat, we’ve looked at how Distributed Denial of Service (DDoS) in IPv6 has increased significantly. In this article, we’ll be diving deeper into the types of attacks and how it can be fended off.
Types of attacks
There are many methods a person can launch a DDoS attack. In this article, we’ll be focusing on the newer methods of attacking, such as spoofing and application layer (L7) attacks.
Spoofing
Spoofing is to modify the IP packet’s source address to another IP address which they do not own. Tools such as hping3 allows you to do so. Spoofing of packets will render all IP based firewall rules useless. Therefore, traditional methods of DDoS protection will not work as effectively.
Packets can be easily spoofed if the service provider does not implement Access Control List (ACL) and some basic security. Sometimes, it is not implemented due to incompetency. While other times, it is intentionally allowed so that the provider would be able to host customers who want to spoof their packets. The shady market is a huge opportunity for these providers to explore into as it is quite profitable.
Some of the providers that allow packet spoofing are:
Spoofed SYN Flood
A SYN flood is to flood a server with a large amount of useless TCP Synchronize “Open” traffic. This would consume the servers’ resources and also saturate the bandwidth with useless traffic. TCP Syncookies would be able to put the flood under control. However, if the traffic is spoofed, it would also be an ineffective method.
Spoofed UDP Flood
A UDP flood is to flood a server with a large amount of useless UDP packets. UDP is fast and allows a large amount of packets to be sent. It consume the routers’ resources as the routers will have to process the large amount of UDP packets. IP based firewall rules would be able to put the flood under control. However, if the traffic is spoofed, it would also be an ineffective method.
L7 attacks
Layer 7 attacks are sophisticated application based DDoS attacks. These attacks are tailored to the specified application just to drain the servers’ resources. Examples of such attacks would include WordPress XMLRPC pingback attacks, Apache slowloris, etc. A more simple attack would be to target POST forms such as a website’s search or registration form.
Amplification
DDoS can be amplified using DNS, NTP and SSDP. These attacks are commonly done through spoofing the source IP address as the victim’s IP.
DNS Amplification
The malicious servers make a spoofed DNS request to public DNS resolver servers, such as OpenDNS. These public DNS resolver servers will then make a DNS reply to the victim’s IP address, even though the victim did not request for it. It is not easy to verify the request as DNS uses UDP protocol, therefore, spoofing of DNS requests can be done very easily. On a large scale spoofed DNS requests, it will wreck havoc on the victim’s servers.
Below is a visual of how it looks like, accompanied by a visual:


NTP Amplification
NTP amplification is yet another type of attack using Network Time Protocol. It is also based on the UDP protocol, which makes spoofing possible. It is very similar to how DNS amplification is done. However, it is able to deal a larger blow as compared to DNS.
SSDP Amplification
Finally, the mother of all mothers. The father of all fathers. SSDP amplification attack. Just by using two 1 Gbit servers, one would be able to dish out a 600Gbps SSDP attack. This is how large this amplification can deal out. It can even destablise websites behind DDoS protection.
DDoS Protection
The above attack methods can be defended against using the following methods:
- Hiding the server origin
- Using DDoS defense firewall
- Using a Web Application Firewall
- Distributing DDoS traffic using anycast
Hide Server Origin
Hiding the server origin means that the attackers would not be able to know your servers’ IP address. This means that the attacks would not be able to directly hit your servers.
DDoS Defense Firewall
There are DDoS firewalls out there that are able to stand against DDoS through heuristic learning and do the necessary filtering on its own.
WAF
A web application firewall is a firewall that is able to filter out application layer based DDoS attacks.
Anycast
For anycasting, the attacks are distributed geographically through anycasted IP addresses.
Take for example, your server is located in Singapore.


The attacker launches a spoofed DDoS attack from all over the world and it brings your site down very easily.
However, if you have servers located worldwide and the IP address is anycasted.
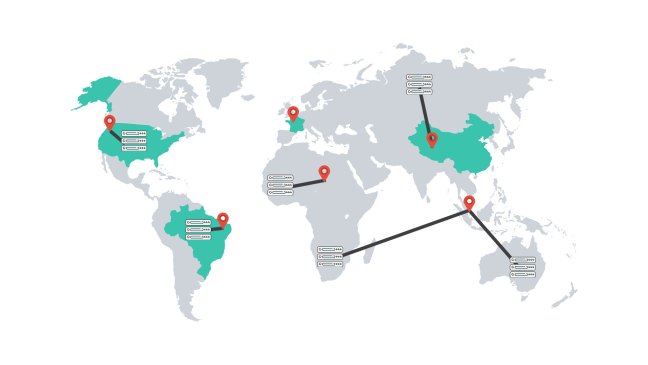
The attacks will only reach the nearest location. This distributes the attacks geographically and shares the traffic load with each other. This decreases the effectiveness of these DDoS attacks.
Solutions
So here are some of the solutions that are available and are quite well known as well.
Cloudflare
Pros:
- Free option
- Hides origin
- WAF option
- Cloud based service
- Anycasted protection
- Enterprise option for DDoS protection
Cons:
- Ineffective if attacker knows server origin IP
- Forced to use their DNS
- Additional costs for protection of non-HTTP/HTTPS ports
Cloudflare offers various plans and some of which, has anycasted DDoS protection. Through their DNS service, web traffic is proxied using their web servers at several edge locations worldwide. This hides your servers’ origin IP address and if the attacker does not know your servers’ origin IP, they would not be able to directly attack your servers. Cloudflare will then filter the traffic on their edge locations. However, this presents an issue as well. If the attacker knows your origin IP, you’re doomed. On top of just typical DDoS protection, they also offer do layer 7 filtering to prevent web application attacks. DDoS protection is only offered on their business and enterprise plan.
Nonetheless, it is a rather affordable service that hides your servers’ origin IP from the attackers and this deters potential attackers from attacking your website.
Riorey
Pros:
- WAF
- On-premise deployment option
- Hybrid deployment option
- Heuristic learning protection
- Enterprise DDoS protection
Cons:
- High deployment costs
Riorey offers a hardware solution to the growing DDoS threat. In addition to hardware solution, they also offer a hybrid cloud and hardware solution, where the firewall communicates with the Riorey cloud to scrub and filter the traffic. Their firewalls can be configured to acts as a WAF to deal with Layer 7 attacks. However, this solution is very expensive and I would not recommend it for SMEs or personal use.
Arbor
Pros:
- WAF
- On-premise deployment option
- Cloud based option
- Heuristic learning protection
- Enterprise DDoS protection
Cons:
- High deployment costs
Similar to the Riorey hardware solution, Arbor offers an on-premise hardware deployment option and a cloud based option. Their firewalls can also be configured to acts as a WAF to deal with Layer 7 attacks.

The on-premise hardware also communicates with the Arbor cloud for traffic scrubbing, if necessary.

However, this solution is very expensive and I would not recommend it for SMEs or personal use.
Amazon Web Services
Pros:
- Free tier option
- WAF option
- Cloud based service
- Anycasted protection
- Enterprise option for DDoS protection
Cons:
- High deployment costs
Amazon Web Service (AWS) is a well known cloud service worldwide and they are currently one of the top few leaders in the cloud industry. AWS’s Elastic Compute has DDoS protection and their protection is able to absorb a large amount of traffic without a scratch. Traffic can be anycasted worldwide and therefore, minimising damage done to a single compute instance. Since inbound traffic is free of charge for most of their regions, you will not need to worry about the costs incurred due to DDoS. They also have tools such as Elastic Beanstalk which allows your traffic to be load balanced, even if it the malicious traffic does not get filtered off initially. On top of these tools, they also have a WAF to defend your website against web attacks.
AWS is an enterprise cloud hosting service and is not very suitable for SMEs or personal usage due to the costs incurred.
Microsoft Azure
Pros:
- Free tier option
- Third-party WAF option
- Cloud based service
- Anycasted protection
- Enterprise option for DDoS protection
Cons:
- High deployment costs
Microsoft Azure is yet another strong competitor in the cloud industry. Their azure network is able to withstand large amount of DDoS traffic without any issues. Traffic can also be anycasted worldwide and therefore, minimising damage done to a single compute instance. Since inbound traffic is free of charge for all their regions, you will not need to worry about the costs incurred due to DDoS. They also have a WAF service offered through a third-party, Barracuda Networks.
Azure is an enterprise cloud hosting service and is not very suitable for SMEs or personal usage due to the costs incurred.
Conclusion
Overall, all of these solutions are quite fantastic. However, depending on your needs and budget, a particular solution might better suit you or your business. For personal website usage, Cloudflare might suit you better because it is an effective yet affordable solution. For personal gameserver usage, a solution like AWS might suit you better because Cloudflare is unable to defend against a non-web service for their free plans.
Ultimately, you still have to know yourself very well and pick your poison.
I hope you enjoyed reading and learnt something from this. If you have any questions, feel free to leave your comments right below. :)




wow man you really have a lot of knowledge on DDOS like a full white hat hacker even though you are a web developer. Mind sharing how you learn all this?